Best Security Solutions for Desktop Tablet Kiosks to Buy in March 2026

monTEK Anti-Theft Tablet Stand, Frameless Universal Tablet Kiosk with Security Lock Fit 7”-15” Screen Size, Compatible with IPad Pro/Air/Mini and Samsung Tab, Black
-
UNIVERSAL COMPATIBILITY: FITS ALL TABLETS 7-15, EASY CHARGING INCLUDED.
-
ENHANCED SECURITY: FEATURES A LOCK TO PREVENT TABLET THEFT EFFORTLESSLY.
-
OPTIMAL VIEWING: 360° ROTATION AND TILT ADJUSTMENT FOR PERFECT ANGLES.



AboveTEK Anti-Theft iPad Kiosk Stand – POS iPad Security Stand & Locking Tablet Holder – Heavy Duty Base, 360° Swivel, 75° Tilt Bracket – Perfect for Retail Business (Black)
- UNIVERSAL FIT FOR MULTIPLE IPAD MODELS FOR VERSATILE USE.
- SECURE LOCKING SYSTEM PROTECTS TABLETS IN HIGH-TRAFFIC ENVIRONMENTS.
- FLEXIBLE DESIGN OFFERS 360° ROTATION FOR OPTIMAL VIEWING ANGLES.



AboveTEK Security iPad Kiosk Floor Stand, Anti-Theft POS Tablet Stands for Retail Business, Height Adjustable Tablet Floor Stand, 360° Swivel Universal Locking Holder Fits 9.7"-13" iPads/iPad Pro/Air
-
UNIVERSAL COMPATIBILITY: SUPPORTS 9.7 TO 13 TABLETS FOR VERSATILE USE.
-
SECURE ANTI-THEFT DESIGN: PROTECTS DEVICES IN HIGH-TRAFFIC AREAS.
-
ADJUSTABLE HEIGHT & 360° ROTATION: CUSTOM COMFORT FOR ANY ENVIRONMENT.



monTEK Anti-Theft Tablet Wall Mount, Universal Tablet Kiosk with Security Lock Fit 7”-15” Screen Size, Compatible with Ipad Series and Samsung Tab, Frameless Design, Black
-
UNIVERSAL FIT: COMPATIBLE WITH ALL TABLETS (7-15) FOR VERSATILE USE.
-
ENHANCED SECURITY: BUILT-IN LOCK KEEPS TABLETS SAFE FROM THEFT.
-
OPTIMAL VIEWING: ADJUSTABLE TILT FROM -25° TO 205° FOR PERFECT ANGLES.


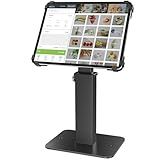
AboveTEK Anti-Theft iPad Kiosk Stand, 360 Rotation & Adj. Height 8.3"–13.4", Heavy-Duty Steel & Aluminum, Fits 9.7"-13" Tablets, Security Retail POS Tablet Stand for Business & Commercial Use
- SECURE TABLETS IN BUSY AREAS WITH LOCKABLE, ANTI-THEFT ENCLOSURE.
- ENJOY 360° ROTATION & ADJUSTABLE HEIGHT FOR OPTIMAL CUSTOMER VIEWING.
- DURABLE ALUMINUM & STEEL DESIGN ENSURES STABILITY IN HIGH-TRAFFIC SPACES.



monTEK Anti-Theft Tablet Floor Stand, Frameless Universal Tablet Kiosk with Security Lock Fit 7-15” Screen, Height Adjustable Mount Compatible with Gen 7 to 10 /iPad Pro/Air/Mini/Samsung Tab, Black
-
UNIVERSAL COMPATIBILITY: WORKS WITH ALL 7-15 TABLETS, INCLUDING IPADS.
-
ROBUST SECURITY: ANTI-THEFT LOCK KEEPS YOUR TABLET SAFE AND SECURE.
-
VERSATILE VIEWING: ADJUSTABLE HEIGHT AND TILT FOR OPTIMAL USER EXPERIENCE.



woleyi Anti Theft Tablet Kiosk Stand for 9"-14" Tablet, Security iPad Desk Floor Stand, Heavy Duty Tablets POS Display Mount with Lock and Key, Compatible iPad Pro 13/Air, Surface Pro/Go, Galaxy Tabs
- SECURE YOUR TABLET WITH A LOCKABLE STAND FOR PUBLIC SETTINGS.
- FLEXIBLE 360° SWIVEL & 270° FLIP FOR OPTIMAL VIEWING ANGLES.
- EASY INSTALLATION AND UNIVERSAL FIT FOR ALL MAJOR TABLET BRANDS.


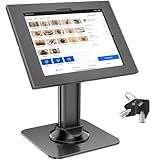
AboveTEK Anti-Theft iPad Kiosk Stand – POS iPad Security Mount with 360° Swivel & 75° Tilt, Heavy Duty Tablet Kiosk Desk Holder for Retail & Business POS Systems (Black)
- UNIVERSAL COMPATIBILITY: FITS VARIOUS IPADS & SAMSUNG GALAXY TABLETS.
- ULTIMATE SECURITY: RELIABLE LOCK SYSTEM PREVENTS THEFT IN ANY SETTING.
- FLEXIBLE VIEWING: 360° ROTATION & 75° TILT FOR PERFECT DISPLAY ANGLES.



AboveTEK Anti Theft iPad Floor Stand, Robust Security Kiosk POS Tablet Stand, Height Adjustable Secure Holder Enclosure w/Lock and Key Mechanism for iPads/iPad Air/iPads Pro, Ideal for Retail Business
- ULTIMATE SECURITY: ADVANCED LOCK MECHANISM PREVENTS THEFT & TAMPERING.
- VERSATILE COMPATIBILITY: FITS VARIOUS IPAD MODELS FOR DIVERSE SETUPS.
- USER-FRIENDLY DESIGN: ADJUSTABLE HEIGHT & TILT FOR OPTIMAL INTERACTION.


To prevent theft of a desktop tablet kiosk, there are several security measures that can be implemented. One way is to physically secure the kiosk by using cables or lockable enclosures to prevent it from being easily picked up or stolen. Additionally, installing security cameras or alarms in the vicinity of the kiosk can act as a deterrent to potential thieves.
Another important measure is to restrict access to the kiosk by implementing password protection or biometric authentication. This can prevent unauthorized users from tampering with or stealing the tablet. Regularly updating the software and firmware of the kiosk can also help to prevent security vulnerabilities that could be exploited by thieves.
Furthermore, monitoring the kiosk regularly, both physically and remotely, can help to detect and prevent theft before it occurs. In case of theft, having a tracking device installed on the kiosk can aid in locating and recovering it. Overall, a combination of physical security measures, access restrictions, regular monitoring, and tracking devices can help to effectively prevent theft of a desktop tablet kiosk.
What is the importance of using strong passwords on a desktop tablet kiosk?
Using strong passwords on a desktop tablet kiosk is important for maintaining security and protecting sensitive information. Strong passwords can help to prevent unauthorized access to the kiosk, which could lead to the theft of confidential data, identity theft, or other malicious activities.
Without a strong password, individuals with malicious intent could potentially gain access to the kiosk and manipulate the system, install malware, or access personal information stored on the device. This can be particularly concerning in public settings where multiple users may have access to the kiosk.
Overall, using strong passwords on a desktop tablet kiosk is essential for maintaining security and safeguarding sensitive data. By creating complex and unique passwords, users can help to minimize the risk of unauthorized access and protect their personal information and privacy.
What is the best way to prevent unauthorized physical access to a desktop tablet kiosk?
There are several ways to prevent unauthorized physical access to a desktop tablet kiosk:
- Use physical barriers such as enclosures and locking mechanisms to secure the tablet in place.
- Implement biometric authentication methods such as fingerprint or facial recognition to restrict access to authorized users only.
- Set up user-specific passwords or PINs that are required to access the tablet kiosk.
- Restrict physical access to the kiosk by placing it in a secure location or using security personnel to monitor the area.
- Enable remote monitoring and management capabilities to track and control access to the kiosk in real-time.
- Educate users on the importance of security measures and the risks associated with unauthorized access to the tablet kiosk.
By implementing these security measures, you can effectively prevent unauthorized physical access to a desktop tablet kiosk and protect sensitive information stored on the device.
What is encryption and how does it protect data on a desktop tablet kiosk?
Encryption is the process of encoding information in such a way that only authorized parties can access it. It converts data into a code to prevent unauthorized access to sensitive information.
In the case of a desktop tablet kiosk, encryption can protect data by securing the data stored on the device. This means that even if the device is lost or stolen, the data will remain safe and inaccessible to unauthorized users. Encryption can also protect data that is being transmitted over a network, such as when a user enters their personal information on a kiosk to make a payment or access their account.
By encrypting data on a desktop tablet kiosk, businesses can ensure that sensitive information remains confidential and secure, helping to prevent data breaches and protect customer privacy.
How to conduct regular security assessments of a desktop tablet kiosk?
conduct regular security assessments of a desktop tablet kiosk by following these steps:
- Perform vulnerability scans: Use a vulnerability scanning tool to regularly scan the kiosk for any potential security vulnerabilities, such as outdated software or misconfigured settings.
- Conduct penetration testing: Hire a third-party security firm to perform penetration testing on the kiosk to identify any potential security weaknesses that could be exploited by attackers.
- Review access controls: Ensure that only authorized users have access to the kiosk and review the access control settings regularly to prevent unauthorized access.
- Update software and firmware: Keep the kiosk's operating system, applications, and firmware up to date with the latest security patches to protect against known vulnerabilities.
- Monitor network traffic: Set up monitoring tools to track network traffic to and from the kiosk, looking for any suspicious activity that could indicate a security breach.
- Implement security best practices: Follow best practices for securing kiosk devices, such as disabling unnecessary services, restricting physical access, and using strong passwords.
- Regularly review security policies: Review and update security policies for the kiosk, including user authentication procedures, data encryption standards, and incident response protocols.
- Train staff: Provide training for staff members who have access to the kiosk on security best practices and how to recognize and report potential security threats.
- Perform regular security audits: Conduct regular audits of the kiosk's security controls and procedures to ensure compliance with security standards and identify areas for improvement.
By following these steps, you can ensure that your desktop tablet kiosk remains secure and protected from potential security threats.
